Ubuntu 24.04 에서 lunch 실행 후 아래와 같은 메세지가 발생했습니다.
Build sandboxing disabled due to nsjail error.
검색해보니 docker나 wsl 환경에서 발생했다는 경우들이 있었고
그 외의 Ubuntu 환경의 경우에 아래의 링크에서 답을 찾을 수 있었습니다.
https://github.com/google/nsjail/issues/110#issuecomment-2322854914
Build sandboxing disabled due to nsjail error. This may become fatal in the future. · Issue #110 · google/nsjail
I was following a tutorial on how to build android. These were the following steps: make clobber source build/envsetup.sh lunch aosp_marlin_userdebug setpaths make -j4 When I execute the lunch and ...
github.com
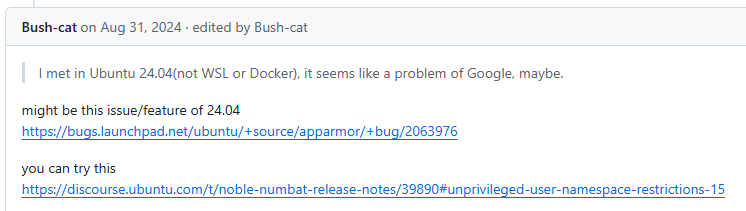
저와 같은 상황 입니다.
https://bugs.launchpad.net/ubuntu/+source/apparmor/+bug/2063976
Bug #2063976 “Apparmor breaking nsjail in AOSP” : Bugs : apparmor package : Ubuntu
Build sandboxing in AOSP is broken after updating to 24.04 with the following denials: [ 182.439078] audit: type=1400 audit(1714265880.641:449): apparmor="AUDIT" operation="userns_create" class="namespace" info="Userns create - transitioning profile" profi
bugs.launchpad.net
Ubuntu 24.04 LTS (Noble Numbat) Release Notes
Noble Numbat Release Notes Table of Contents Introduction New features in 24.04 LTS Known Issues Official flavours More information Introduction These release notes for Ubuntu 24.04 LTS (Noble Numbat) provide an overview of the release and document the kno
discourse.ubuntu.com
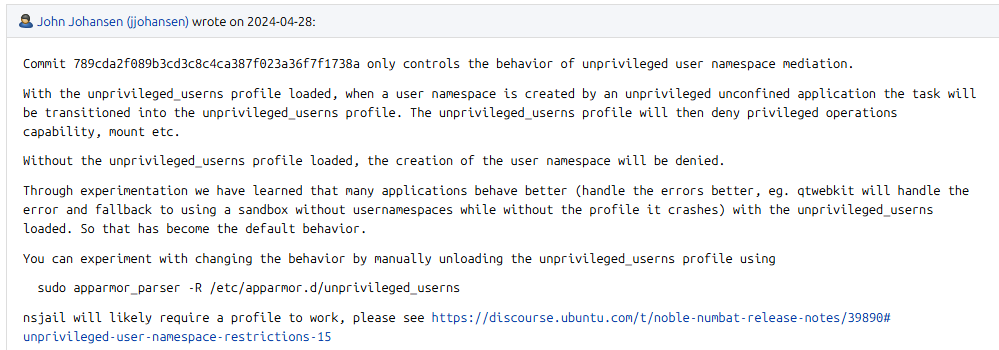
Unprivileged user namespace restrictions
In combination with the apparmor package, the Ubuntu kernel now restricts the use of unprivileged user namespaces. This affects all programs on the system that are unprivileged and unconfined. A default AppArmor profile is provided that allows the use of user namespaces for unprivileged and unconfined applications but will deny the subsequent use of any capabilities within the user namespace. A common use-case for unprivileged user namespaces is applications that construct their own sandboxes or work with styles of container workloads. As such, AppArmor profiles that allow the use of unprivileged user namespaces are also provided for common applications and frameworks that come from the Ubuntu archive, as well as popular third party applications like Google Chrome, Discord and others. This is a subsequent step towards trying to mitigate the larger attack surface presented by unprivileged user namespaces (the first being the introduction of this feature in Ubuntu 23.10 where it was not enabled by default).
임시 해결책은 아래와 같이 적용합니다.
echo 0 | sudo tee /proc/sys/kernel/apparmor_restrict_unprivileged_userns
영구적인 적용 방법은 아래와 같습니다.
/etc/sysctl.d/60-apparmor-namespace.conf 파일 생성
$ cat /etc/sysctl.d/60-apparmor-namespace.conf
kernel.apparmor_restrict_unprivileged_userns=0reboot 후 적용.
'Android' 카테고리의 다른 글
| AOSP에 디바이스를 추가하는 과정. (0) | 2025.02.19 |
|---|---|
| Sparse file header (0) | 2024.11.14 |
| Android partitions (3) | 2024.10.18 |
| Sparse file (0) | 2024.10.16 |

